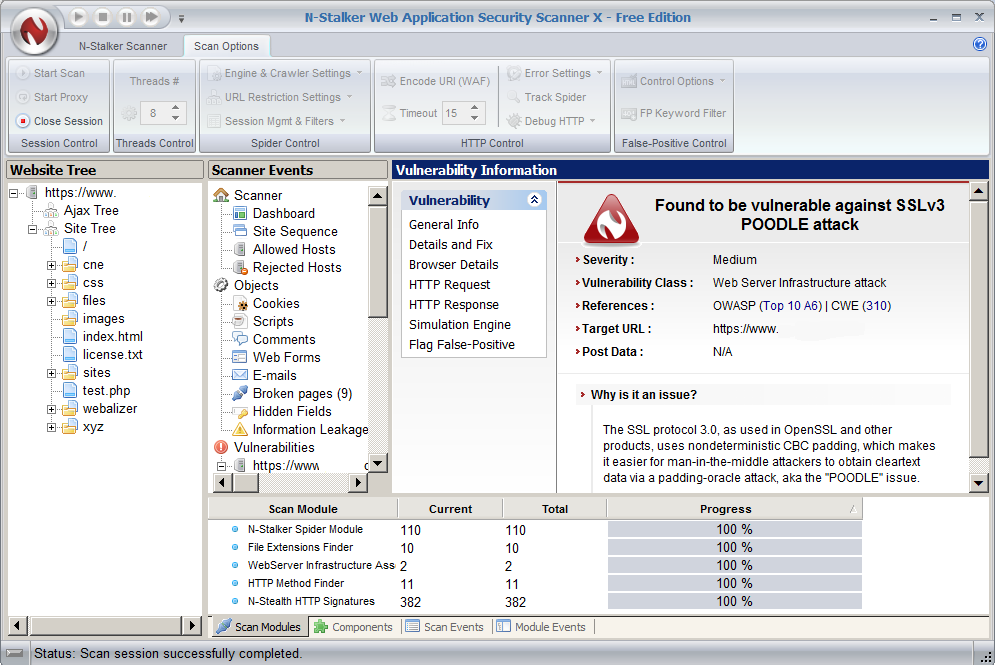
Using N-Stalker to detect POODLE vulnerability in SSL
N-Stalker Web Application Security Scanner can help you detect if your supporting Web servers are relying on SSLv3 protocol to establish encrypted connections with your web clients. According to the latest advisory from Google Security Team, a vulnerability in the design of SSL version 3.0 can be used to calculate the plaintext of secure connections by a network attacker, allowing for an effective man-in-the-middle attack against SSL tunnels. The problem was uncovered by Bodo Möller, Thai Duong and Krzysztof Kotowicz from Google.
The problem cannot be patched or fixed within the SSLv3 protocol, so this version of SSL/TLS framework must be disabled to stop further attacks. It’s been more than 18 years since the release of version 3.0 and new versions of the TLS protocol are already in place, however, modern web servers and browsers are still supporting old versions to avoid breaking up compatibility with old clients. POODLE is clearly a final call for ending up the old SSLv3 support (just like version 2). See more technical details about the vulnerability here.
Both N-Stalker Free or Commercial Editions can be used to detect support for SSLv3: